As long as people have existed there has been someone out there plotting up new ways to con or scam you out of your possessions.
Spam is more than just a nuisance filling up your inbox with useless junk. Spam can pose a real threat. Often spam e-mails contain links to malicious code that can infect your computer or mobile device. Those junk messages can also try and phish for information to later be used for identity fraud. They can also be a straight up scam offering you something that is too good to be true.
With the ubiquity of the internet ever present in our lives a breed of internet schemers has been born. How can you detect a scam? What can you do if you encounter one? How can reduce the number of unsolicited requests?
Should I Stay or Should I Go
While there is no single rule for determining if something is legit there are a few guidelines you can follow. Use common sense. Take the second to ask yourself:
- Is this from someone I know and trust?
- If it’s from a supposed organization (like the government, financial institution, charity) ask yourself is it normal for them to be contacting me by email, and not in writing or by phone?
- Is it professionally written without spelling mistakes or grammatical errors?
- Are they asking me for money or personal information?
- Promising something unbelievable?
- Look at the address and the links of the website or email do they match the place they claim to be coming from?
- Are they threatening me with something and creating a sense of urgency?
- If it’s from your bank, credit card, cell phone company or other supplier. Ask yourself is this how they normally contact me? Go to their website or call them and verify the information. IMPORTANT DO NOT CLICK ON THE LINK IN THE EMAIL/NOTIFICATION/OR ANSWER THE QUESTIONS ON THE PHONE CALL. Instead go directly to their website, or call their 1-800- number directly to confirm it was indeed from them.
If you think it’s not legit don’t open it! You can delete the entire spam folder without opening a single message. If you think it may be from someone you know and it’s misidentified as junk then do not click on any links, or open any attachments, unless you’re 100% certain it’s legitimate.
What if it’s not that obvious; go with your gut. If you have any doubts try looking it up on Snopes.com the definitive Internet reference source for urban legends, folklore, myths, rumors, and misinformation. Even just Google it!
Latest types of internet scams and spam you should be aware of in 2025
- AI-Powered Scams: Scammers are now using artificial intelligence (AI) to enhance existing scams. For instance:
- They create more convincing and natural-sounding phishing emails and text messages using AI.
- Deepfakes of celebrities are used to trick victims into thinking they’re investing in legitimate companies or projects.
- Impersonation of victims’ friends or relatives occurs in scams like the grandparent scam.
- Scammers may even impersonate employers to extract personal information.
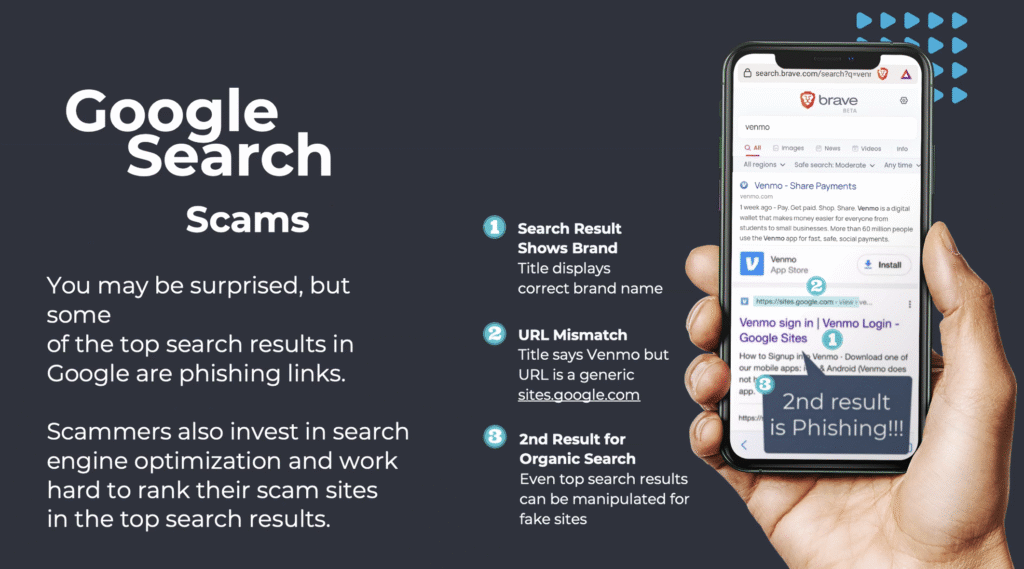
- Google Search Scam: Often you will search for a company, software or app to update or login to instead of typing in the URL. The first few items that appear at the top of the Google results are often paid advertisements that scammers can pay for to trick you into clicking on a link that takes you to a a nefarious website that gets you to enter personal information or install malware.
- Student Loan Forgiveness Scams: When student loan forgiveness applications opened in 2022, scammers started targeting applicants. They trick people into believing they can help with the application process, only to steal personal information and money.
- Cryptocurrency-Romance Scam: Scammers combine crypto scams with old-fashioned romance scams, posing as internet love interests so they can cajole their targets into downloading an app and investing in fake crypto accounts.
- Payday Loan Scam: Criminals exploit the inflation squeezing workers by offering fake payday loans that they claim will help people settle their bills. Loan applicants are told they’ll need to prepay a fee. The money goes into the crooks’ pockets, and the applicant gets nothing.
- Phishing and Smishing Scams: Cybercriminals send emails, or text messages, appearing to be from a legitimate source, such as a bank or online store. They trick victims into clicking on a malicious download or a scammer website link, then install malware and/or use stolen credentials to steal sensitive data.
- Ransomware: A cybercriminal may infect your computer with malware called ransomware. Once installed, the cyberthief could encrypt your files and demand a ransom payment, typically in a cryptocurrency such as Bitcoin.
- Scareware: Scareware can come in a couple of forms, but possibly the most common of this internet scam is fake antivirus software. A pop-up alerts you of a virus that infected your device. It then offers to fix the infection with “free antivirus” software. This software is indeed fake and used to install malware that can steal your sensitive information.
- Travel Scams: Online scammers send an email pretending to be a travel insurance agent. Their well-designed but fake email convinces you to purchase travel insurance for a trip you recently booked. They record and misuse your personal banking information.
- Fake Shopping Websites: Cyberthieves may also create and publish fake shopping websites that either look genuine or replicate existing retailer websites. They typically feature deals that are too good to be true, finding popular brands of clothing and expensive electronics at extra-low prices.
- Phone Scams: Scammers contact victims by phone with Robocalls (automated calls) that use increasingly natural-sounding recorded voices, offering everything from auto warranties to vacations. Scammers also pretend to be IRS personnel, police, survey takers, relatives, delivery people, or well-known companies to threaten or gain trust.
Pig Butchering Scams
A “pig slaughtering scam,” or “Pig Butchering Scam,” also known as a “sha zhu pan” scam, is a type of online investment fraud. The term comes from the metaphor of fattening a pig before slaughter, which in this context means gradually building trust with a victim before defrauding them. Even younger more tech savvy people have fallen victim to this type of scam. Here’s how it typically works:
- Contact: Scammers create fake online personas and contact potential victims through social media, dating apps, or direct messaging platforms.
- Trust Building: Over time, they build a relationship with the target, often feigning romantic interest or friendship.
- Investment Lure: The scammer then introduces the idea of an investment opportunity, usually involving cryptocurrency, and shows fake evidence of high returns to persuade the victim to invest.
- Increasing Investments: Victims are encouraged to invest small amounts initially, which appear to yield high returns due to manipulated dashboards or fake claims.
- The Slaughter: Once the victim is sufficiently ‘fattened’ by investing larger sums, the scammer disappears with the funds12.
These scams can be quite sophisticated, with scammers often spending weeks or months to groom their victims. It’s important to be cautious when someone you’ve met online seems overly eager to discuss investment opportunities, especially if they involve cryptocurrency12. Always verify the legitimacy of any investment platform and be wary of unsolicited investment advice from strangers online. Watch this entertaining and enlightening video about Pig Butchering scams from Last Week Tonight with John Oliver.
So you have determined it’s a scam what do you do?
Usually you can just delete the message, notification, or post. However, you can also be a good ‘netizen’ by reporting the fraud to the RCMP (info@antifraudcentre.ca)! If you’ve already given out personal or financial information then start contacting your bank, credit bureau, and local police, in addition to reporting the email to the Canadian Anti-Fraud Centre. The Get Cyber Safe initiative by the Government of Canada dedicated to frauds and scams with a wealth of information.
Protect Yourself and Prevent Identity Theft
- In addition to being vigilant you can set up spam or junk mail filters in your email program. WBC Designs offers professional spam filtering at the server level for emails hosted by us. Add it to your account.
- Use a reputable email provider or client (e.g. Gmail or Thunderbird). They have up to date databases to identify and classify emails as spam.
- Use a primary email address for friends and colleagues and use a completely separate email address for online activities like filling out forms or joining online communities.
- Never reply to, or click on a “remove” or “unsubscribe” link in a suspicious spam message. If you do respond, it will confirm your address and cause you to receive more spam.
- Never click on any links in sketchy messages or on suspect websites.
- Keep your software and Operating System up to date. Regularly update your computer, browser, software, and mobile devices. Updates often include security patches to protect against new threats.
- Make sure you have trusted anti-virus software which is updated and protects against malicious software (malware).
- Never click on any window that pops up on your computer screen claiming that your system has been infected.
- Don’t open attachments in your emails unless you know what you’re opening and where it’s from…
- Whenever possible, enable multi-factor authentication on your accounts. This adds an extra layer of security, making it harder for scammers to gain access to your information. For example, needing a code sent to your phone by text message or using an authenticator app.
- Use strong, unique (never reuse the same) passwords for each of your online accounts. Consider using a password manager to help you create and store complex passwords.
- Avoid using public Wi-Fi for banking, shopping, or entering personal information online. Unsecured networks can be easily hacked and your information can be stolen.
- Be cautious about the personal information you share on social media. Scammers can use information you share to answer security questions and gain access to your accounts.
- Block Robocalls and Robotexts: First never respond to unwanted calls and texts. If you do they know your number is valid and it will just increase your frequency of receiving these unwanted calls and texts. Never click on any links either. You can enable Spam Protection on your Android smartphone and Filter Unknown Senders on an iPhone. Some cellular carriers also offer a way to block spam callers and texts before they get to you. There are also apps you can install. To find out in more detail how to block robocallers and stop spam texts click on the links.
There are a billion and one different shams out there and there’s no better way to protect yourself than using your judgment. However, you can improve your judgment by educating yourself about some of the most common techniques and what you can do to protect yourself.
DOUBLE BONUS: Are people not receiving your emails because they are being marked as junk? Check the spammyness of your emails with this handy tool. Also check to see if your email has been compromised on this site: haveibeenpwned.com.




